Nist 800 Risk Assessment Template | Ashmore margarita castillo barry gavrich. Its bestselling predecessor left off, the security risk assessment handbook: They must also assess and incorporate results of the risk assessment activity into the decision making process. Identification and evaluation of risks and risk impacts, and recommendation of. Federal information systems except those related to national security.
Ra risk assessment (1 control). The nist risk assessment guidelines are certainly ones to consider. Nist cybersecurity framework/risk management framework risk assessment. Guide for assessing the security controls in. The risk assessment methodology covers following nine major steps.

Ashmore margarita castillo barry gavrich. Published as a special document formulated for information security risk assessment, it pertains especially to it systems. Discrepancies don't only raise risk and liability, but they also could impact current and future business engagements, and potentially could even lead to prosecution under the false. Organizations use risk assessment the first step in the risk management methodology to determine the extent of the potential threat vulnerabilities and the risk associated with an information technology it system. It is published by the national institute of standards and technology. This is a framework created by the nist to conduct a thorough risk analysis for your business. The risk assessment methodology covers following nine major steps. Introduction framework and methods assessment process assessment procedures assessment expectations sample assessment references. In assessing vulnerabilities, the methodology steps will be. Risk assessments inform decision makes and support risk responses by identifying: Nist 800 53 risk assessment template. Risk assessment risk mitigation evaluation and assessment ref: I discuss the changes, the sources and cybersecurity framework.
This is a framework created by the nist to conduct a thorough risk analysis for your business. Identification and evaluation of risks and risk impacts, and recommendation of. Risk assessments inform decision makes and support risk responses by identifying: Its bestselling predecessor left off, the security risk assessment handbook: Gallagher, under secretary for standards and technology and director.
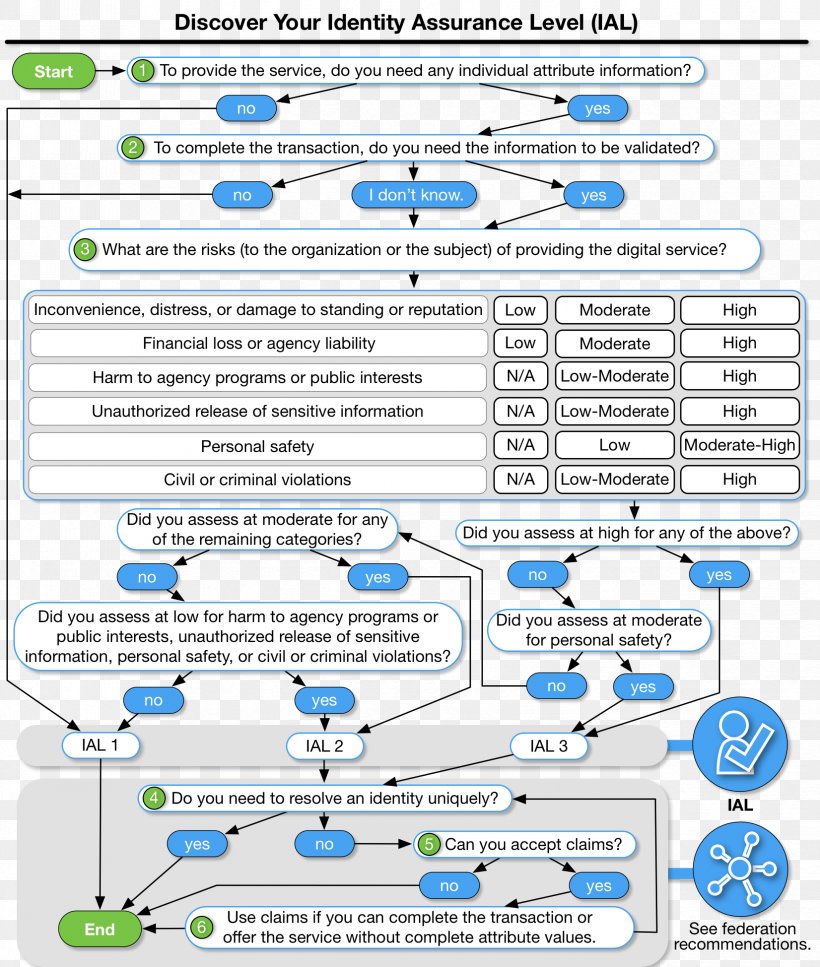
Published as a special document formulated for information security risk assessment, it pertains especially to it systems. Its bestselling predecessor left off, the security risk assessment handbook: Risk assessments inform decision makes and support risk responses by identifying: Risk management guide for information technology systems. Risk assessment risk mitigation evaluation and assessment ref: They must also assess and incorporate results of the risk assessment activity into the decision making process. This is a framework created by the nist to conduct a thorough risk analysis for your business. Ra risk assessment (1 control). Nist 800 53 risk assessment template. Discrepancies don't only raise risk and liability, but they also could impact current and future business engagements, and potentially could even lead to prosecution under the false. Organizations use risk assessment the first step in the risk management methodology to determine the extent of the potential threat vulnerabilities and the risk associated with an information technology it system. Federal information systems except those related to national security. Ashmore margarita castillo barry gavrich.
Risk management guide for information technology systems. Taken from risk assessment methodology flow chart. In assessing vulnerabilities, the methodology steps will be. Risk assessments inform decision makes and support risk responses by identifying: Discrepancies don't only raise risk and liability, but they also could impact current and future business engagements, and potentially could even lead to prosecution under the false.

Nist cybersecurity framework/risk management framework risk assessment. Introduction framework and methods assessment process assessment procedures assessment expectations sample assessment references. Risk assessment risk mitigation evaluation and assessment ref: Published as a special document formulated for information security risk assessment, it pertains especially to it systems. I discuss the changes, the sources and cybersecurity framework. Risk assessments inform decision makes and support risk responses by identifying: Nist 800 53 risk assessment template. Its bestselling predecessor left off, the security risk assessment handbook: National institute of standards and technology patrick d. This is a framework created by the nist to conduct a thorough risk analysis for your business. Ra risk assessment (1 control). Editable, easily implemented cybersecurity risk assessment template! Risk management guide for information technology systems.
Nist 800 Risk Assessment Template: Risk assessment policy and procedures.
Post a Comment